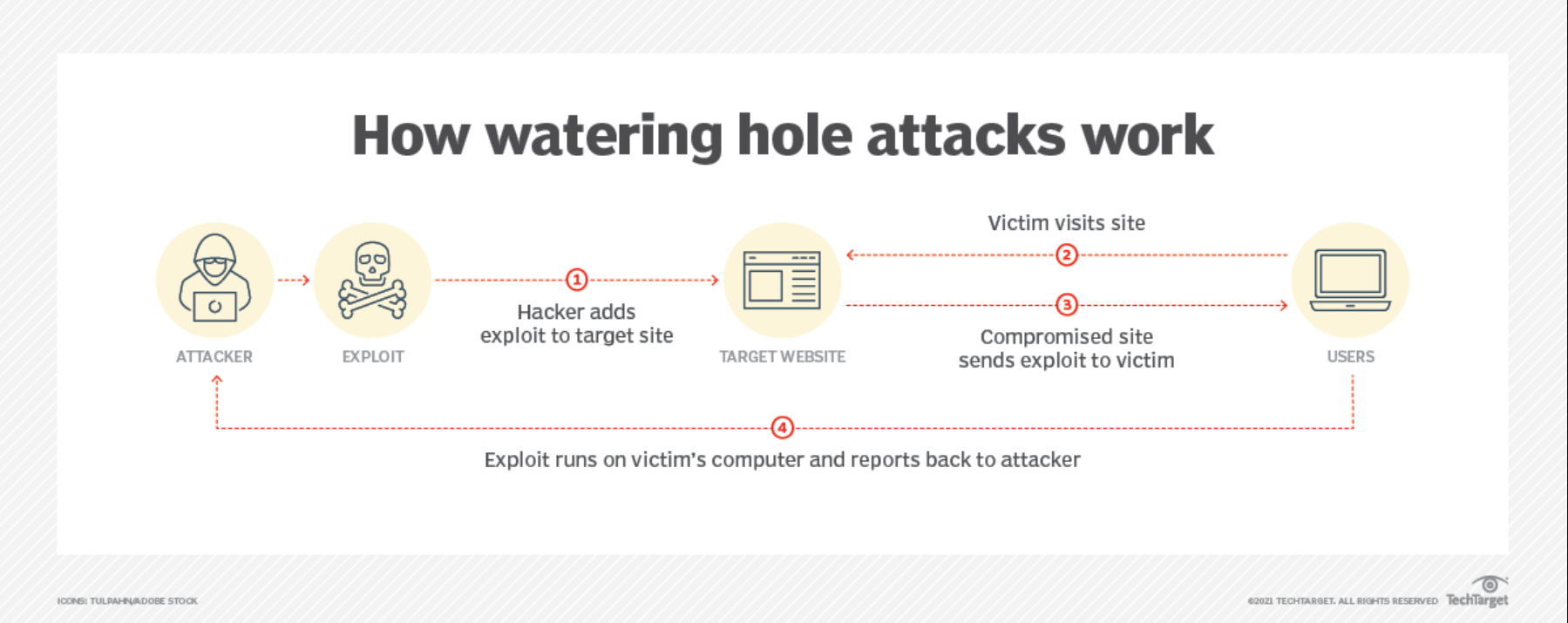
A watering hole attack is a scenario where a cybercriminal compromises or inserts malware into a legitimate website, thereby gaining access to an organization’s website or computer system. This watering hole attack is likened to animal predators, who wait patiently for their prey to emerge and then pounce on them when they are unaware. The hacker prefers this attack method because he does not need to break into the secure sites of the organization, they only need to target and infect less protected organizations that have links with the secure ones. Whenever the secured organizations launch into the websites of their vulnerable partners, they automatically become vulnerable and open to attack.
What makes a Watering Hole Attack unique
Watering hole attacks leverage victims’ trust in familiar websites. It compromises the websites that are frequently visited by individuals or organizations, making them susceptible to attacks. Unlike other attacks that focus on financial gain or data theft, watering hole attacks are often used for spying purposes, surveillance or intelligence-gathering purposes. It is difficult to detect and prevent a watering hole attack because hackers make use of legitimate websites and networks to carry out their acts. This attack targets high-value establishments such as government agencies, financial institutions, and large enterprises.
Prevention and Mitigation of Watering Hole Attack
- Constantly update operating systems, and browsers with the latest software and operating system patches.
- Educate and train employees on watering hole attacks. Improving employees’ security awareness helps to reduce fling into traps and lowers the risk of downloading malware from web pages.
- Organizations should regularly backup data, to ensure that data can be easily restored in the event of loss.
- Install and regularly update your antivirus software.
- Make use of firewalls to detect and prevent malicious traffic from making unauthorized access to the system.
- Routine checks like Security audits, vulnerability assessments and penetration testing should be carried out periodically. All identified gaps should be covered quickly.
- There should be clear boundaries between work and personal resources even in environments that operate BYOD
Motivations Behind Watering Hole Attack
Different individual attackers and groups are responsible for watering hole attack. Governments, criminal organizations, and activist groups are perpetrators of this attack. They do this for financial gain, political or ideological motivation, intellectual property theft, personal gain, disruption of operations, Surveillance and so on.
 Source
Source