Microsoft has been in the news for the past couple of months. Beginning in July 2023, it was reported to have been compromised by the Threat Actor Group ‘Storm-0558’, a group of Chinese origin. The Threat Group reportedly stole signing keys which they abused to forge authentication tokens-granting them access to the inboxes of individuals working for the United States government.
Recently, Microsoft unveiled the findings of its ongoing technical investigation, presenting a detailed account of the tactics employed by the attackers during the security breach.
Background of the attack
May 15, 2023: Storm-0558 utilized counterfeit authentication tokens to gain unauthorized access to user email accounts across approximately 25 organizations, encompassing government agencies and associated consumer accounts hosted on public cloud platforms.
Actor overview
Storm-0558 is a China-based threat actor with TTPs(Tactics, Techniques, and procedures) consistent with cyber espionage. While minimal similarities have been discovered with other Chinese groups such as Violent Typhoon (ZIRCONIUM, APT31), it is believed that Storm-0558 operates as an independent and distinct group.
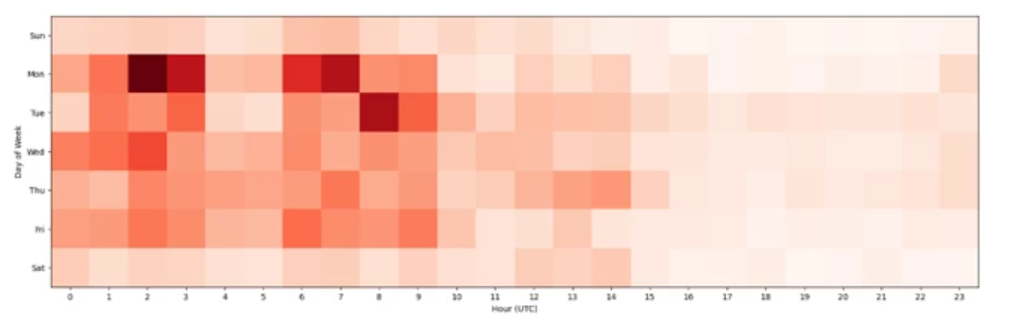
The figure above shows the heatmap of observed Sorm-0558 activity by day of week and hour (UTC). The heatmap data, collected between April and July 2023 showed that the actor’s core working hours are consistent with working hours in China Monday through Friday from 12:00 AM UTC (8:00 AM China Standard Time) through 09:00 AM UTC (5:00 PM China Standard Time).
Storm-0558 has so far primarily targeted US and European diplomatic, economic, and legislative governing bodies, as well as individuals connected to Taiwan and Uyghur geopolitical interests. Previously, Storm-0558 targeted think tanks, media companies, and telecommunications equipment and service providers.
Each Storm-0558 campaign has sought to obtain unauthorized access to email accounts belonging to employees of targeted organizations. Storm-0558 pursues this objective through credential harvesting, phishing campaigns, and OAuth token attacks.
Storm-0558 has also displayed an interest in OAuth applications, token theft, and token replay against Microsoft accounts since at least August 2021, operating with a high degree of technical tradecraft and operational security.
Microsoft also observed that Storm-0558 obtained credentials for initial access through phishing campaigns. The actor has also exploited vulnerabilities in public-facing applications to gain initial access to victim networks. These exploits typically result in web shells, including China Chopper, being deployed on compromised servers. One of the most prevalent malware families used by Storm-0558 is a shared tool tracked by Microsoft as Cigril. This family exists in several variants and is launched using dynamic-link library (DLL) search order hijacking.
After gaining access to a compromised system, Storm-0558 accesses credentials from various sources, including the LSASS process memory and Security Account Manager (SAM) registry hive.
Recent Campaign
On June 16, 2023, Microsoft was notified by a customer of anomalous Exchange Online data access. Microsoft analysis attributed the activity to Storm-0558 based on established prior TTPs. From the analysis, Microsoft was able to determine that Storm-0558 was accessing the customer’s Exchange Online data using Outlook Web Access (OWA); later discovering that the actor was forging Azure AD tokens using an acquired Microsoft account (MSA) consumer signing key. This was made possible by a validation error in Microsoft code.
In response to this threat, Microsoft swiftly took action by blocking the use of forged tokens, replacing the compromised key, and engaging in collaborative efforts with the affected organizations to resolve the issue.
Read here for more details about the campaign
How the MSA Signing key was accessed
Microsoft, during the course of their investigation, discovered that the MSA signing key was stolen from a Windows crash dump. April 2021 saw a crash in the consumer signing key, one in which the MSA key used was leaked into a crash dump.
A Microsoft engineer’s account had access to the debugging environment, which contained the crash dump with the key. Storm-0558 actors gained access to the dump after compromising the engineer’s corporate account.
Typically, crash dumps should not contain signing keys, however, a race condition allowed the key to be leaked into the crash dump according to Microsoft.
Microsoft further states that, due to log retention policies, they do not have logs with specific evidence of the key’s exfiltration.
What did Microsoft do?
Microsoft took the following steps in the wake of the attack;
- Revoked all valid MSA signing keys and resolved the race condition issue responsible for the key’s inadvertent exposure in a crash dump.
- Strengthened prevention, detection, and response for key material inadvertently included in crash dumps.
- Improved credential scanning to better identify the presence of the signing key in the debugging environment.
- Released enhanced libraries designed to automate key scope validation within authentication libraries and provided clarifications in related documentation.
Additional measures implemented by Microsoft and the full Microsoft analysis of Storm-0558 techniques for unauthorized email access can be found here
Have a security incident to report? Send an email to help@cchub.africa