The focus this month is on the new NIST Framework 2.0, HrServ a previously unknown web shell used in a recent APT attack, LummaC2 stealer’s novel Anti-Sandbox technique, the DarkGate Loaders, and the fall of Lockbit. Please keep reading to stay updated with the latest Intelligence updates from our Command Center.
NIST Framework 2.0
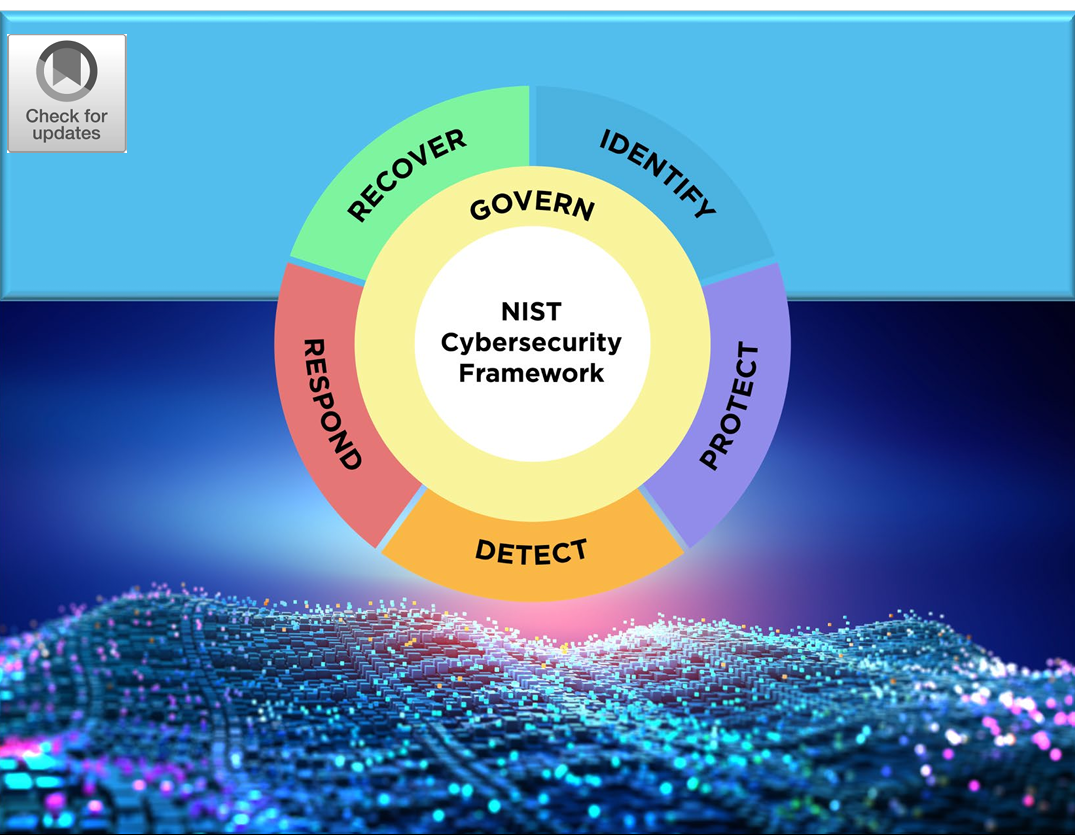
The National Institute of Standards and Technology officially released the second version of its highly-rated Framework, NIST Cybersecurity Framework (CSF) 2.0 which guides industry, government agencies, and other organizations to manage cybersecurity risks.
Summary
- It is divided into three (3) components; CSF Core, CSF Organizational Profiles, and CSF Tiers.
- Builds on the existing five (5) basic functions of Identify, Protect, Detect, Respond, and Recover with an additional function in ‘Govern’.
- NIST CSF 2.0 also addresses supply chain risks.
- Read more about the NIST CSF 2.0 here
HrServ – Previously unknown web shell used in APT attack
Summary
- A previously unknown web shell called HrServ has been discovered, exhibiting sophisticated features such as custom encoding methods for client communication and in-memory execution.
- The initial infection occurs through the creation of a scheduled task on the system, which executes a .BAT file that copies the HrServ.dll file to the System32 directory and configures a service via the registry.
- The HrServ web shell initiates an HTTP server and uses custom encoding techniques for client-server communication, including Base64 encoding and FNV1A64 hashing algorithms.
- The web shell has different code execution processes based on the value of a GET parameter in the HTTP request. It can create a new thread, create a file and write POST data to it, read a file and append it to a response, return Outlook Web App HTML data, and more.
- The web shell is associated with financially motivated malicious activity due to its characteristics and operational methodology, but it also exhibits similarities with APT behaviour.
Read the full report here
LummaC2 stealer’s novel Anti-Sandbox technique: Leveraging trigonometry for human behaviour detection
Summary:
- LummaC2 v4.0 is an information stealer specialising in acquiring and exfiltrating sensitive information from compromised devices.
- The malware has undergone updates and is currently on version 4.0, with new features such as Control Flow Flattening obfuscation and an Anti-Sandbox technique.
- The Anti-Sandbox technique leverages trigonometry to detect human behaviour by analyzing mouse movement, delaying the detonation of the malware until human-like behaviour is detected.
- The malware uses a packer to obfuscate the malicious payload and facilitate its execution without spawning additional processes.
- The malware also includes a feature to prevent the execution of unpacked samples, forcing threat actors to use a crypter for their builds.
Analyzing DarkGate Loaders
Summary
- DarkGate is a commodity malware that has been around since late 2017/early 2018 and is being used by initial access brokers to provide access to networks for other threat actors, including ransomware groups.
- DarkGate has recently been distributed through phishing campaigns using malicious attachments sent via Microsoft Teams.
- Three different loader types used in recent DarkGate infections have been identified: MSI Loader, VBScript Loader, and JavaScript Loader.
- The MSI Loader is signed and wrapped using a MSI Wrapper from exemsi.com, and it downloads and executes the AutoIt3 executable and the .au3 script.
- The VBScript Loader includes non-malicious printer-related functions to confuse analysis, and it also uses cmd and curl to download the AutoIt3 executable and the .au3 script.
- The JavaScript Loader is heavily obfuscated and uses an ActiveXObject to download the AutoIt3 executable and the .au3 script.
- Defenders should monitor additional communication channels for initial DarkGate delivery, including Microsoft Teams, and can block or limit external domains on applications like Teams or Skype to prevent users from receiving messages or files from unknown entities.
The Fall of LockBit

Summary
- On 19 February, the UK’s National Crime Agency (NCA), working with the FBI and other national police forces, seized control of the LockBit extortion website.
- The joint operation, between the NCA, the FBI, Europol, and a coalition of international police agencies, was revealed with a post on LockBit’s own website, which read: “This site is now under the control of the National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, Operation Cronos.”
- Europol stated that two LockBit actors were arrested in Poland and Ukraine; with a further two thought to be affiliates arrested and charged in the US.
- Authorities also froze over 200 cryptocurrency accounts linked to the LockBIT organization.
- LockBit is a cybercriminal group proposing ransomware as a service (RaaS). Software developed by the group (also called ransomware) enables malicious actors who are willing to pay for using it to carry out attacks in two tactics where they not only encrypt the victim’s data and demand payment of a ransom but also threaten to leak it publicly if their demands are not met.
- According to a joint statement by various government agencies, LockBit was the world’s most prolific ransomware in 2022. It was estimated in early 2023 to be responsible for 44% of all ransomware incidents globally.
- In the United States between January 2020 and May 2023, Lockbit was used in approximately 1,700 ransomware attacks, with US$91 million paid in ransom to hackers.
Sources
- https://www.nist.gov/cyberframework
- https://securelist.com/hrserv-apt-web-shell/111119/?utm_source=podia&utm_medium=broadcast&utm_campaign=1713865
- https://outpost24.com/blog/lummac2-anti-sandbox-technique-trigonometry-human-detection/?utm_source=podia&utm_medium=broadcast&utm_campaign=1713865
- https://blog.pulsedive.com/analyzing-darkgate-loaders/?utm_source=podia&utm_medium=broadcast&utm_campaign=1713865
- https://www.theguardian.com/technology/2024/feb/20/uk-and-fbi-lock-cybercrime-group-out-of-lockbit-website