Midnight Blizzard
Midnight Blizzard (also known as Cozy Bear, and APT29) is a Russian hacker group allegedly affiliated with one or more Russian intelligence agencies. The group has been identified as the Advanced Persistent Threat group, APT29, reportedly behind the 2020 SolarWinds supply-chain attacks where trojanized software updates were used to infect thousands of the managed security service provider (MSSP) customers.
Campaign
The group’s most recent campaign involved the use of credential theft phishing messages sent via Microsoft Teams chats. The actors use compromised Microsoft 365 tenants belonging to small businesses to create new domains that pose as technical support entities. These are then used to send lures through Teams messages to deceive users into approving multifactor authentication (MFA) prompts. When successful, the hackers are provided with the targeted organization’s credentials.
For the operation to be successful, Midnight Blizzard either already has valid credentials for the users being targeted or targets users with passwordless authentication set on their accounts. Both require the user to enter a code displayed during the authentication flow.
Following the successful deception, the actor gains access to the user’s Microsoft 365 account, allowing them to steal information from the compromised tenant.
How to identify the attack
- Targeted users receive a Microsoft Teams message request from an external user pretending to be a technical support or security team staff.
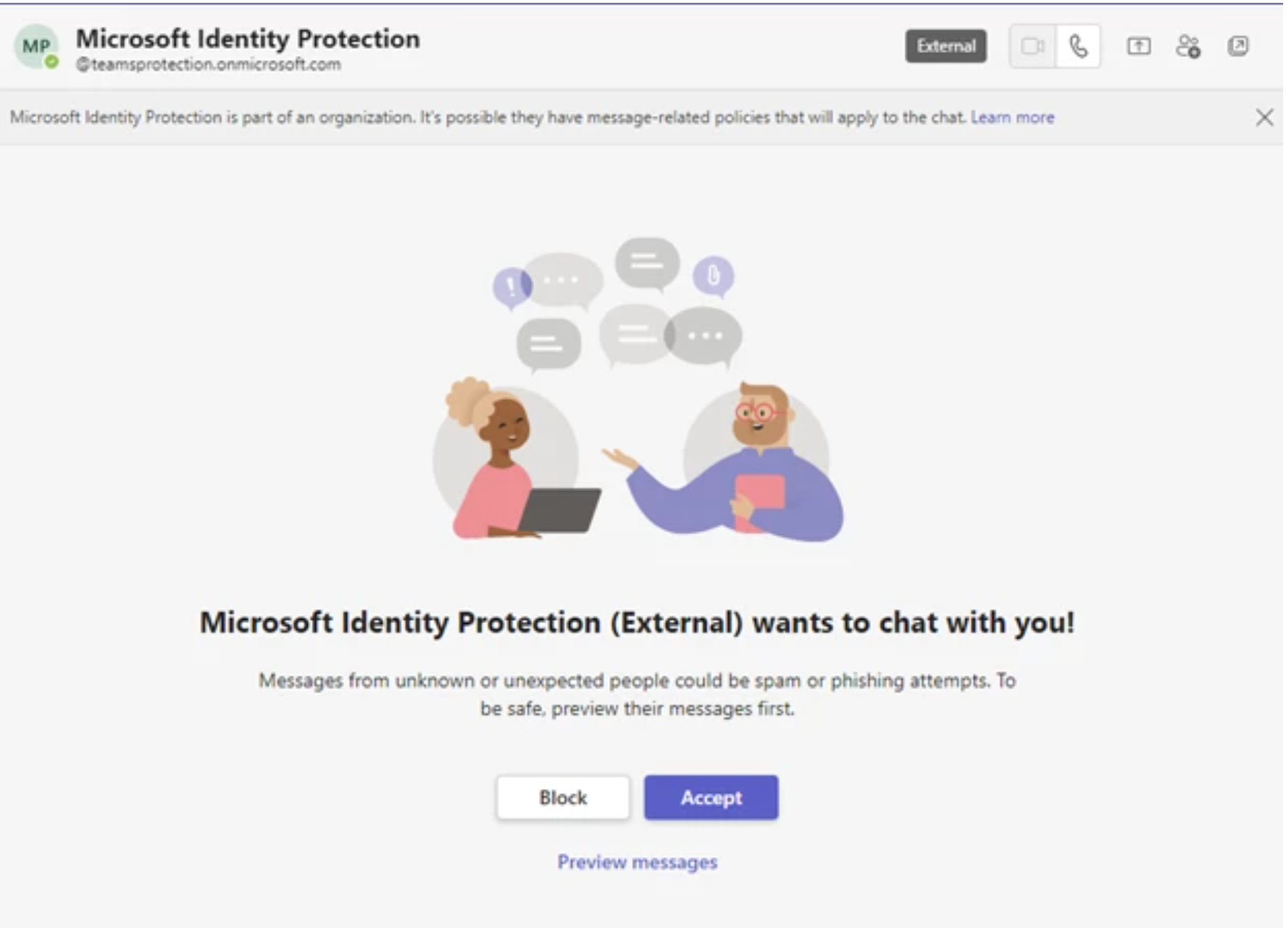
- If the user accepts the request, they receive a message that attempts to convince them to enter a code into their Microsoft Authenticator app on their mobile device.
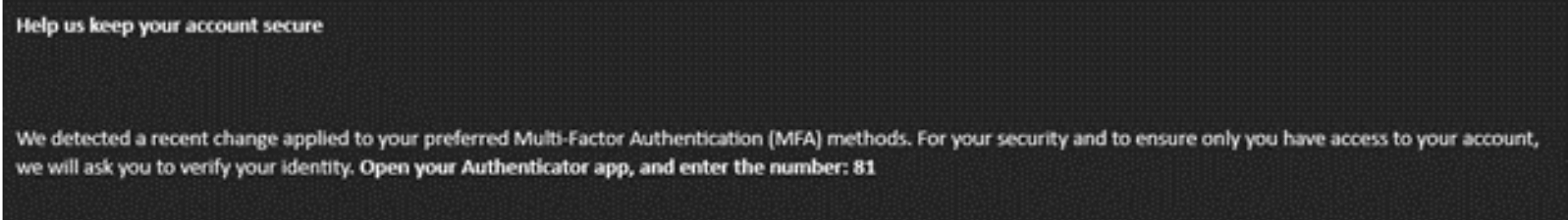
- If the message request is successfully accepted by the user, the threat actor is granted a token to authenticate as the targeted user, completing the authentication flow and automatically gaining access to the user’s Microsoft 365 account.
Indicators of Compromise (IOC’s)
Domains:
- msftprotection.onmicrosoft[.]com
- identityVerification.onmicrosoft[.]com
- accountsVerification.onmicrosoft[.]com
- azuresecuritycenter.onmicrosoft[.]com
- Teamsprotection.onmicrosoft[.]com
Recommendations
Microsoft recommended the following to mitigate the risk of the threat.
- Pilot and start deploying phishing-resistant authentication methods for users.
- Implement Conditional Access authentication strength to require phishing-resistant authentication for employees and external users for critical apps.
- Specify trusted Microsoft 365 organizations to define which external domains are allowed or blocked to chat and meet.
- Keep Microsoft 365 auditing enabled so that audit records could be investigated if required.
- Understand and select the best access settings for external collaboration for your organization.
- Allow only known devices that adhere to Microsoft’s recommended security baselines.
- Educate users about social engineering and credential phishing attacks, including refraining from entering MFA codes sent via any form of unsolicited messages.
- Educate Microsoft Teams users to verify ‘External’ tagging on communication attempts from external entities, be cautious about what they share, and , and never share their account information or authorize sign-in requests over chat.
- Educate users to review sign-in activity and mark suspicious sign-in attempts as “This wasn’t me”.
Implement Conditional Access App Control in Microsoft Defender for Cloud Apps for users connecting from unmanaged devices.