The discussions on spyware began in the 1990s, but in the early 2000s, cybersecurity firms decided to describe it as an unwanted software that spied on their user’ and computer activity. The first anti-malware spyware was launched in June 2000, and four years later, scans showed that about 80% of internet users had their devices affected by spyware, according to the research by American Online and the National Cybersecurity Alliance.
Spyware can be defined as malicious software designed to enter your computer device, gather data from the device and user, and forward it to a third party without your consent. It can also be referred to as legitimate software that monitors your data for commercial purposes, like advertising. Note that malicious spyware is explicitly used to generate profit from stolen data. Spyware follows a three-step process from being installed on a device to sending or selling the information it has stolen. They are;
- Infiltrate – via application install packages, malicious websites, or file attachments.
- Monitor and capture – Once the spyware is installed, it follows the user around the internet, capturing the data they use, stealing their information, login credentials, and passwords via keystrokes, screen captures, and other tracking codes.
- Send stolen data – the attacker sends stolen data to the spyware author, to be used directly or sold to other parties.
Data compromised by spyware often includes collecting confidential information such as;
- Login credentials (Password and Username)
- Account PINs
- Credit card number
- Monitored keyboard strokes
- Tracked browsing habits
- Harvested email addresses
Keyloggers as a form of Spyware
Keylogger is a type of software that is commonly associated with spyware, which is any authorized or malicious software installed to secretly monitor user activity and/or gather data which is stored on a compromised computer. This form of spyware captures every keystroke you type; they can send this information to remote servers, where login information; including passwords, can be extracted and used.
How Keyloggers Infiltrate Devices
Keyloggers are spread in different ways, but all have the same purpose. They can access your device if they are installed or plugged into your computer. Keyloggers gain unauthorized access to your device in the following ways:
- Drive-by download: This is a type of malware that installs itself on a victim’s system without their knowledge. This happens when they visit a compromised or harmful website. It takes advantage of browser or software flaws to quietly install a keylogger. This keylogger then records and steals your keystrokes.
- Spear Phishing: This is a key method of initiating malware infection. It entails using phishing emails or links to target customers. This link looks legitimate, but after you click on it, the malware installs a keylogger on your device.
- Trojan Horse: It is common for Trojan horses to have keyloggers bundled inside. A Trojan horse is malware that looks like a real program. It secretly installs a keylogger to capture and steal your keystrokes. The malware tracks every keystroke after it’s installed. Then, it sends this information to the hacker’s devices.
- Web page scripts are a type of malicious code that captures user input on a webpage and sends it to an attacker. Unlike traditional keyloggers, these do not require installing malware on the victim’s device.
Real-World Scenarios of Keylogging
IT security researchers at Checkpoint, a cybersecurity firm in Israel and the US, discovered that a Nigerian hacker gained access to more than 4,000 computers in energy companies spanning over 5 countries in the MENA region in a distributed attack. This was done through phishing and malware infection. The hacker used a Remote Access Trojan and a keylogger to steal targeted organisations’ login details and financial information. The remote access trojan took control of infected systems. The keylogging program then stole login credentials. The attacks were directed towards the financial staff employed in different sectors and regions of the firm. Link
Signs that spyware is on your device
In today’s digital landscape, detecting spyware on a device can be straightforward or extremely difficult, depending on its complexity. Consumer-grade spyware, such as stalkerware or keyloggers, can sometimes be identified using antivirus or anti-spyware tools. Keyloggers, in particular, are widely used to silently record everything a user types, including passwords and private messages, making them a serious threat to privacy. Advanced spyware, like state-sponsored tools such as Pegasus, is built to remain hidden and often evade detection entirely without forensic-level analysis. Factors like device type, operating system restrictions (especially on iPhones), and low user awareness all contribute to why such threats often go unnoticed. Subtle signs like battery drain, unusual app behavior, or unexplained data usage are often the only clues.
There are signs to watch out for that may indicate your device has been compromised. Firstly, you may experience unexpected device battery drain, overheating and unnecessary malfunctioning of your device’s operating system and apps. Your device location and GPS settings may change frequently. Secondly, using more cellular data than normal could indicate that information is being sent from your device without your knowledge, and if you are also experiencing trouble turning off your device completely, it could be another warning sign of spyware activity.
Furthermore, certain types of spyware designed to generate illicit profit may gain sufficient access to affect your financial accounts. If you find yourself subscribed to services or plans without your consent, it could indicate the presence of spyware. Pro tip – Monitor your bank statement for any unusual or unauthorized charges.
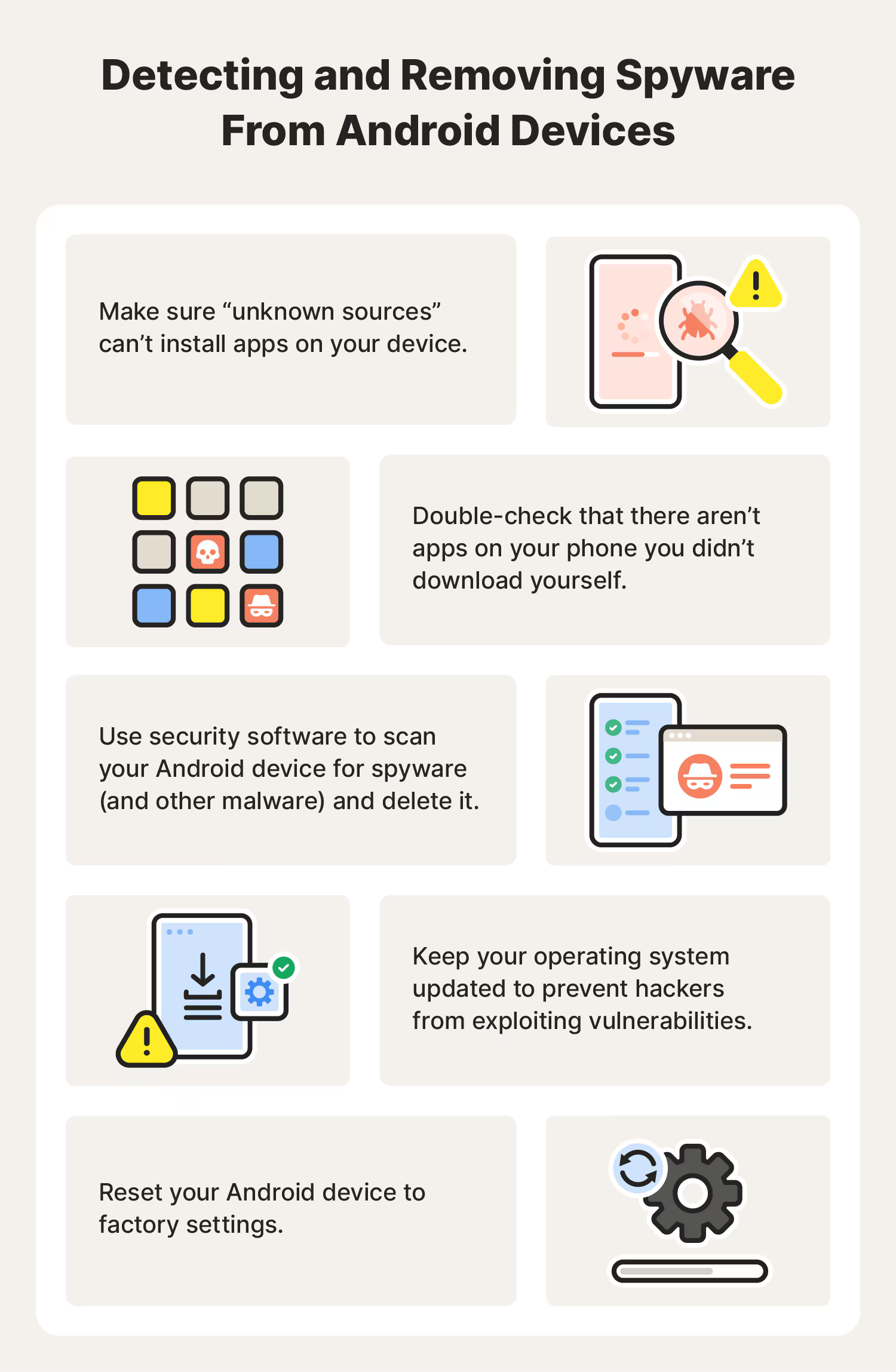
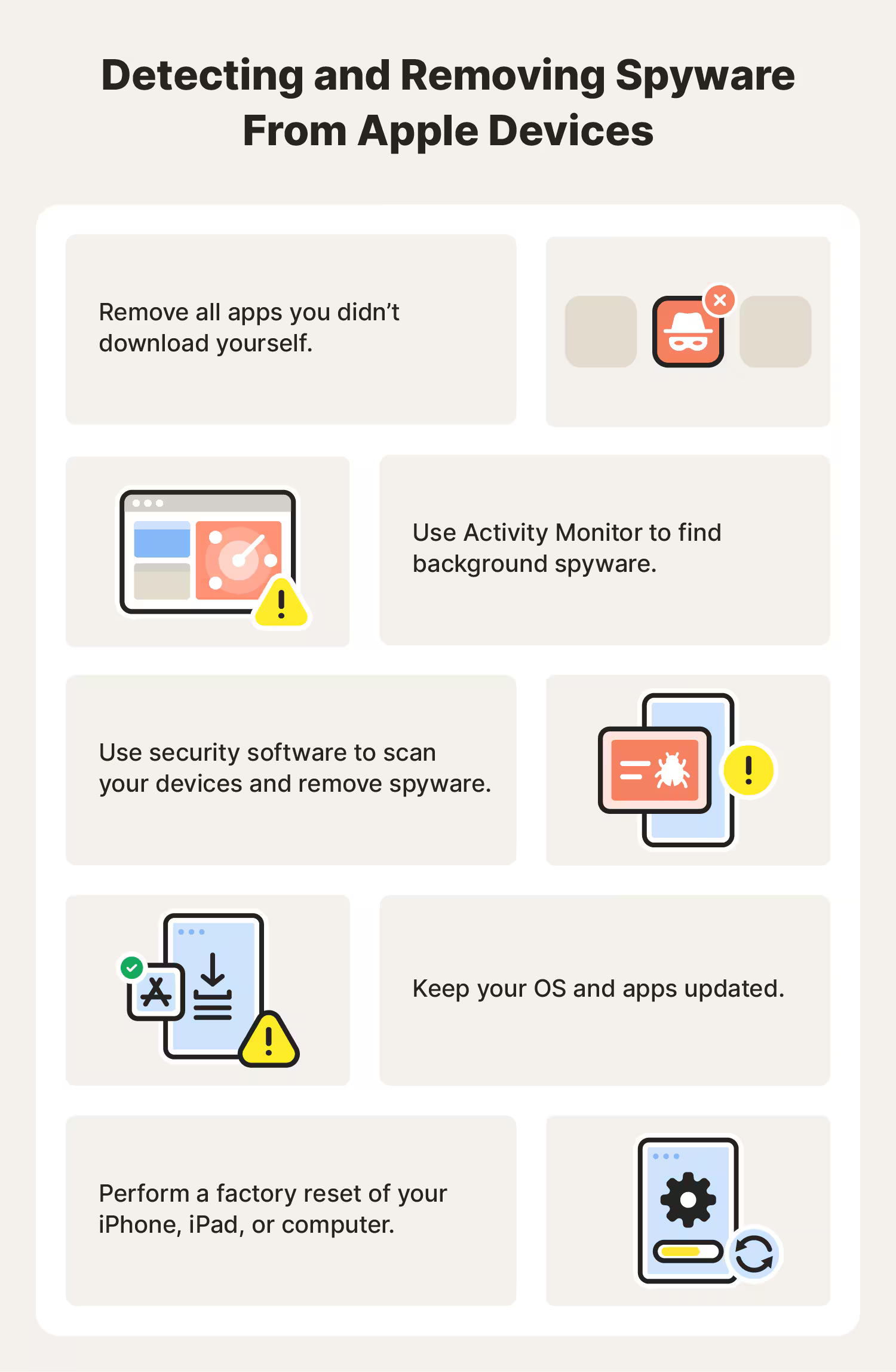
How to remove spyware
- Run a full scan on your computer with anti-virus software: Some anti-malware software may not find the spyware when it is monitoring your computer in real time, but it can detect and eliminate spyware during a full system scan. Set your anti-virus software to run a full scan periodically.
- Use a dedicated spyware removal tool: Endeavor to use software specifically designed to detect and remove spyware from reputable firms, as one of the most common ways to package spyware is by disguising it as anti-malware software.
- Delete suspicious applications on your device: Go through the installed apps on your device and delete any app you do not recognize.
- Check device administration: Ensure that no suspicious applications have administrator privileges. If so, remove it.
- Update your operating system: New versions of the operating system come with security patches and upgrades, which can come with spyware. Always keep this updated.
SOURCES
- https://www.fortinet.com/resources/cyberglossary/spyware#:~:text=Spyware%20is%20malicious%20software%20that,device%20without%20the%20user’s%20consent.
- https://www.kaspersky.com/resource-center/threats/spyware
- https://www.crowdstrike.com/en-us/cybersecurity-101/cyberattacks/keylogger/
 Link
Link